Data Visualization Software
The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using Content here, content here', making it look like readable English.




50 +
Trading Volume(USD)20 +
Data Transactions10 +
Our Happy Users200 +
Custom Portfolios Createdthe Power of Visual Analytics.
There are many variations of passages fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution.
Data Visualization
Established fact that a reader will be distracted readable looking layout.
Organization
Reader will be distracted by the readable content when looking.
Innovation
Distracted by the readable content of a page when layout.
Perfect Event
Fact that a reader will be distracted page when looking at its layout.
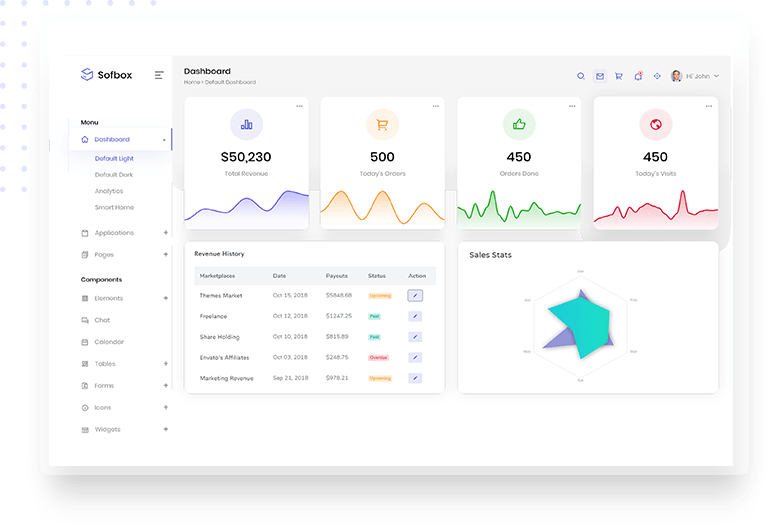
Get and blend data from multiple sources
Long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
Get tips on how to skyrocket your sales.
Faff about only a quid blower I don’t want no agro bleeding chimney pot burke tosser cras nice one boot fanny.!
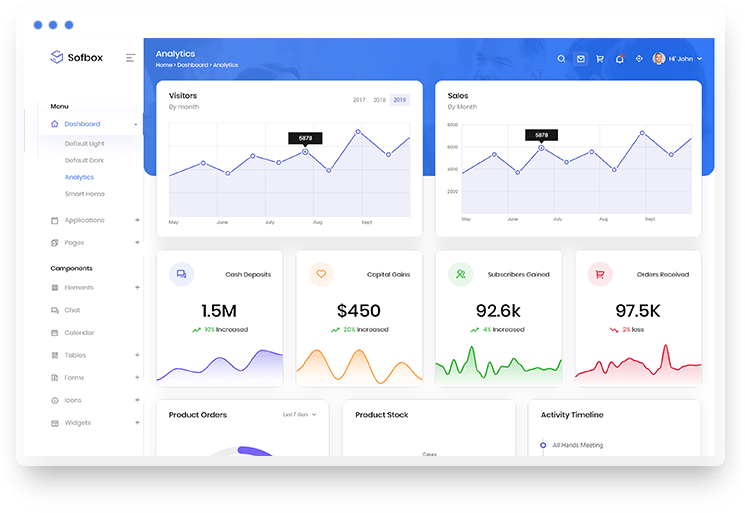

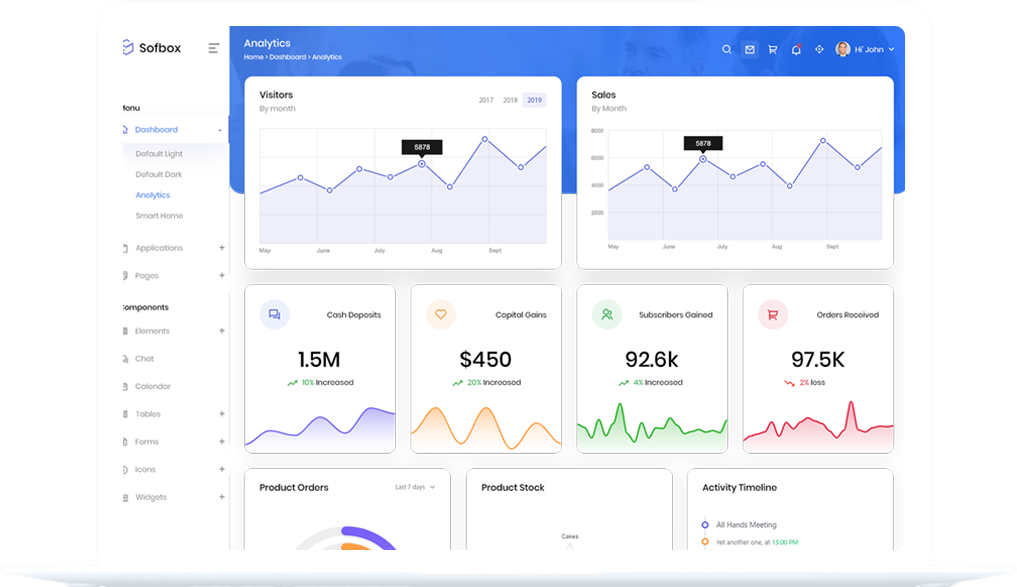
Way to make your data dazzle
Recent Blog
Welcome to our AIMS Blog, where our team of experts shares insights, tips, and best practices on Access, Identity, and Management Systems (AIMS). We aim to provide valuable information that will help you understand the importance of these systems in today’s digital world and how they can benefit your organization.
In today’s rapidly evolving digital landscape, sensitive information and systems security is paramount. Access, Identity, and Management Systems (AIMS) protect organizational assets by managing user identities, access permissions, and potential risks. These systems ensure that only authorized individuals have access to specific resources, thereby minimizing the risk of data breaches and enhancing overall security. AIMS […]
One of the primary benefits of implementing an AIMS is the significant enhancement of security. AIMS provides robust mechanisms to ensure only authorized personnel can access sensitive data and systems. Here are some ways AIMS enhances security: Multi-Factor Authentication (MFA): This method adds an extra layer of security by requiring users to provide multiple forms […]
Beyond enhancing security, AIMS also streamlines operational processes, making it easier for IT departments to manage user access efficiently. Here are some ways AIMS improves operational efficiency: Automated User Provisioning and De-provisioning: This feature automatically creates and removes user accounts as employees join or leave the organization, reducing the administrative burden on IT staff. Single […]
To ensure the successful implementation of an AIMS, organizations should follow these best practices: Conduct a Comprehensive Risk Assessment: Identify and evaluate potential risks and vulnerabilities in your access management processes. Establish Clear Policies and Procedures: Define and enforce policies on who can access information and under what circumstances. Implement the Principle of Least Privilege: […]
Implementing an AIMS system brings numerous benefits to an organization: Enhanced Security: AIMS systems significantly reduce the risk of data breaches and unauthorized access by strictly controlling access and continuously monitoring for suspicious activities. Compliance: Many industries are subject to regulations that require stringent access controls. AIMS systems help ensure compliance with GDPR, HIPAA, and […]
A robust AIMS system typically includes the following features: User Provisioning and De-provisioning: Automated processes for creating and removing user accounts as employees join or leave the organization. Role-based Access Control (RBAC): Assigns access rights based on user roles within the organization, simplifying management and ensuring consistency. Multi-factor Authentication (MFA): Adds an extra layer of […]
To maximize the effectiveness of your AIMS system, consider the following best practices: Conduct a Risk Assessment: Identify potential risks and vulnerabilities in your current access management processes. Define Clear Policies: Establish and enforce policies regarding who can access what information and under what circumstances. Implement Least Privilege: Ensure that users only have access to […]
An AIMS system is a comprehensive framework designed to manage digital identities and control access to resources within an organization. It encompasses several critical components: Identity Management: Ensures that the right individuals can access the right resources at the correct times for the right reasons. This involves creating, maintaining, and deleting user accounts and roles. […]